In today’s digital landscape, conducting regular IT security assessments has become essential for organizations seeking to protect their critical assets and maintain effective cybersecurity posture. As threat actors deploy increasingly sophisticated attack methods and regulatory requirements grow more stringent, a structured approach to evaluating security controls is no longer optional—it’s a fundamental business requirement. This comprehensive guide explores how to perform effective IT security assessments in 2025, providing actionable strategies, methodologies, and best practices to help you identify vulnerabilities, evaluate risks, and strengthen your organization’s security stance.
An IT security assessment serves as a systematic evaluation of your organization’s information security posture, examining the effectiveness of security controls, identifying vulnerabilities, and assessing compliance with relevant standards and regulations. According to recent industry research, organizations that conduct comprehensive security assessments at least quarterly experience 63% fewer successful breaches and detect threats 2.5 times faster than those performing assessments annually or less frequently. Throughout this guide, you’ll learn the step-by-step process for planning, executing, and reporting on IT security assessments that deliver tangible value in protecting your business from evolving cyber threats.
Table of Contents
Understanding Modern IT Security Assessments
What Is an IT Security Assessment?
An IT security assessment is a structured process for evaluating your organization’s security controls, identifying vulnerabilities, and determining your overall security posture. Unlike simple vulnerability scans, comprehensive security assessments examine technical, operational, and organizational factors that impact your security effectiveness.
Modern IT security assessments typically include:
- Vulnerability identification: Discovering technical weaknesses in systems, applications, and networks
- Control effectiveness evaluation: Assessing how well security measures function in practice
- Compliance verification: Determining adherence to relevant standards and regulations
- Risk assessment: Analyzing potential impacts and likelihood of security incidents
- Remediation planning: Developing strategies to address identified issues
In 2025, effective IT security assessments have evolved from point-in-time exercises to continuous evaluation processes that adapt to changing threat landscapes and organizational environments.
Types of IT Security Assessments
Several assessment types are commonly used, often in combination, to provide comprehensive security insights:
- Vulnerability Assessment: Identifies and classifies security vulnerabilities in systems and applications
- Penetration Testing: Simulates real-world attacks to test security control effectiveness
- Risk Assessment: Evaluates potential threats and their impacts on business operations
- Compliance Assessment: Examines adherence to specific standards or regulations
- Security Architecture Review: Analyzes the design and implementation of security systems
- Red Team Exercise: Conducts comprehensive attack simulations across multiple vectors
- Social Engineering Assessment: Tests human susceptibility to manipulation techniques
According to recent industry data, organizations implementing multiple assessment types experience 76% greater visibility into security vulnerabilities compared to those using single-methodology approaches.
Evolution of Security Assessment Approaches
Security assessment methodologies have transformed significantly in recent years:
- Traditional Approach (Pre-2020): Periodic, compliance-focused assessments performed annually
- Risk-Based Era (2020-2022): Adaptive assessments focused on business-critical systems and data
- Continuous Assessment Model (2023-Present): Ongoing evaluation integrated with security operations
- AI-Enhanced Assessments (2024-2025): Machine learning augmentation of human assessment capabilities
In 2025, leading organizations have adopted integrated assessment frameworks that combine continuous automated monitoring with targeted in-depth evaluations. This hybrid approach delivers 82% more effective vulnerability identification compared to traditional periodic assessments.
Preparing for an Effective IT Security Assessment
Defining Scope and Objectives
A successful assessment begins with clearly defined parameters:
- Assessment Boundaries: Determine which systems, applications, and processes will be evaluated
- Exclusions: Identify what will not be included in the assessment
- Primary Objectives: Define specific goals (compliance verification, vulnerability discovery, etc.)
- Success Criteria: Establish how assessment effectiveness will be measured
- Constraints: Acknowledge limitations such as time, resources, or operational restrictions
Organizations with well-defined assessment scopes report 64% higher satisfaction with assessment outcomes and 47% more actionable findings compared to those with loosely defined parameters.
Assembling the Assessment Team
The right expertise is essential for comprehensive security evaluation:
- Team Composition: Include security analysts, system administrators, compliance specialists, and business stakeholders
- Required Skills: Technical expertise, regulatory knowledge, risk assessment capabilities, and communication skills
- Internal vs. External Resources: Determine whether to use internal staff, external consultants, or a hybrid approach
- Roles and Responsibilities: Clearly define who will perform specific assessment tasks
- Communication Channels: Establish how the team will share information and report issues
According to industry research, assessments conducted by diverse teams with both technical and business expertise identify 73% more business-critical vulnerabilities than purely technical assessments.
Selecting Assessment Methodologies
Choose appropriate evaluation approaches based on your objectives:
- Standards-Based Assessment: Following established frameworks like NIST CSF, ISO 27001, or CIS Controls
- Scenario-Based Evaluation: Testing security against specific threat scenarios
- Technical Testing: In-depth examination of technical controls and configurations
- Process Review: Evaluation of security procedures and practices
- Hybrid Approaches: Combining multiple methodologies for comprehensive coverage
Organizations implementing customized assessment methodologies aligned with their specific risk profiles report 58% more effective vulnerability discovery compared to those using generic approaches.
The IT Security Assessment Process: Step-by-Step
Phase 1: Information Gathering and Planning
The initial phase focuses on collecting essential information:
- Document Review: Examine existing security policies, procedures, and previous assessment reports
- Asset Inventory: Catalog systems, applications, data repositories, and infrastructure components
- Network Mapping: Create or update network diagrams showing interconnections and boundaries
- Control Identification: Document existing security controls and protection mechanisms
- Threat Intelligence Integration: Incorporate relevant threat data for your industry and environment
Organizations that conduct thorough information gathering identify 67% more significant vulnerabilities during the assessment phase.
Phase 2: Vulnerability Discovery and Assessment
This phase focuses on identifying security weaknesses:
- Automated Scanning: Deploy vulnerability scanners across in-scope systems
- Configuration Review: Examine system setups against security benchmarks
- Manual Testing: Perform hands-on evaluation of critical systems
- Code Review: Assess application code for security flaws
- Cloud Security Posture Assessment: Evaluate cloud environment configurations
According to recent data, combining automated scanning with manual testing identifies 3.4 times more critical vulnerabilities than automated scanning alone.
Phase 3: Penetration Testing and Validation
Verify vulnerabilities through simulated attacks:
- External Penetration Testing: Attack simulation from outside the network
- Internal Penetration Testing: Testing from within the network perimeter
- Application Security Testing: Targeting web and mobile applications
- Social Engineering: Testing human susceptibility to manipulation
- Physical Security Testing: Evaluating physical access controls
Organizations conducting comprehensive penetration testing as part of their IT security assessment discover that 38% of critical vulnerabilities cannot be identified through scanning alone.
Phase 4: Risk Analysis and Prioritization
Evaluate the significance of identified issues:
- Vulnerability Categorization: Classify findings by type and affected systems
- Impact Assessment: Determine potential business consequences of exploitation
- Likelihood Evaluation: Assess probability of successful exploitation
- Risk Scoring: Assign priority levels based on impact and likelihood
- Remediation Prioritization: Rank issues based on business risk
Effective risk prioritization enables organizations to address the most critical 20% of vulnerabilities that typically account for 80% of security risk.
Phase 5: Reporting and Communication
Document and communicate assessment results effectively:
- Executive Summary: Provide high-level overview for leadership
- Technical Details: Document comprehensive findings for IT teams
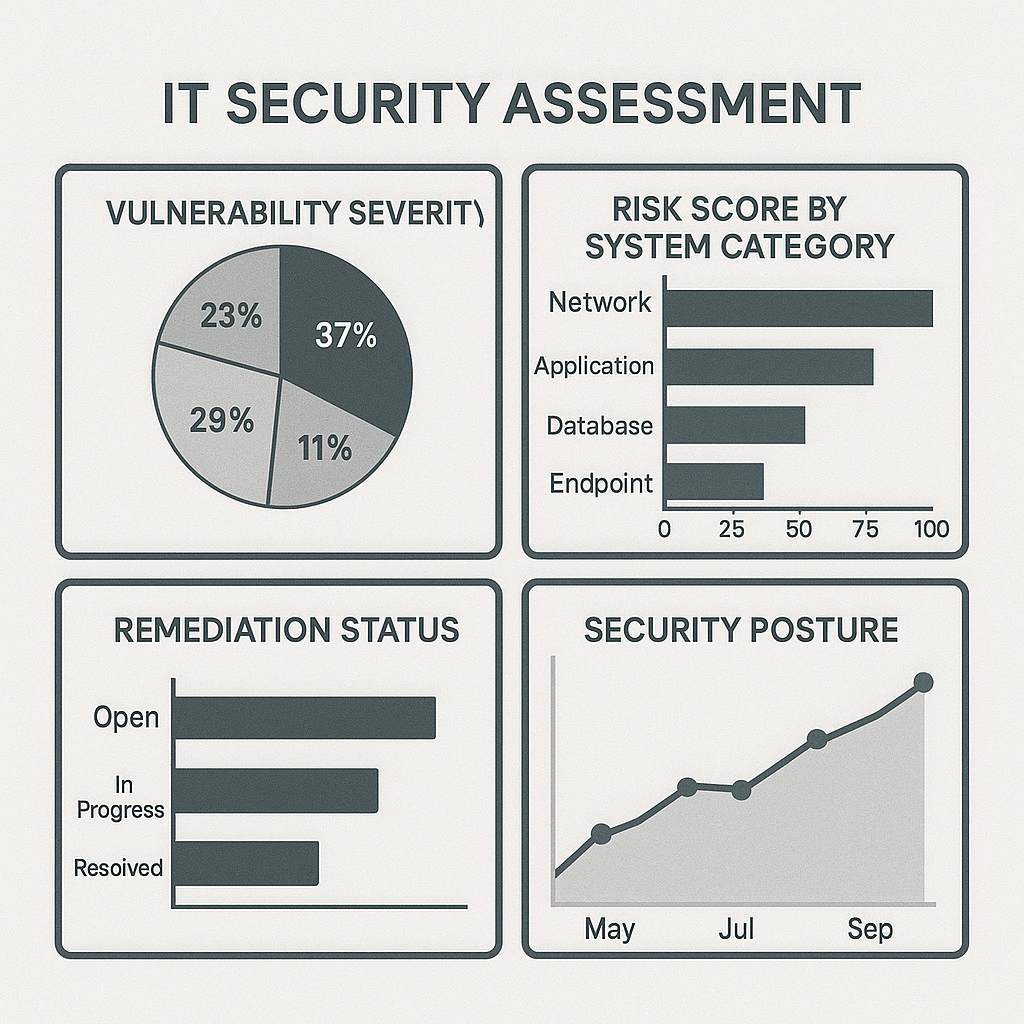
- Risk Visualization: Create clear representations of security issues
- Remediation Recommendations: Provide specific guidance for addressing findings
- Stakeholder Briefings: Present results to relevant audiences in appropriate detail
Organizations using tiered reporting approaches with audience-specific details report 76% higher remediation completion rates compared to those using one-size-fits-all reports.
Essential Tools for Modern IT Security Assessments
Vulnerability Management Platforms
Comprehensive platforms for discovering and tracking vulnerabilities:
- Qualys Vulnerability Management: Cloud-based scanning with continuous monitoring
- Tenable Nessus Professional: Comprehensive vulnerability assessment
- Rapid7 InsightVM: Risk-based vulnerability management
- OpenVAS: Open-source vulnerability scanning
- Microsoft Defender for Endpoint: Integrated endpoint assessment capabilities
According to market research, organizations using integrated vulnerability management platforms identify 58% more vulnerabilities and remediate them 47% faster than those using standalone scanners.
Penetration Testing Tools
Specialized tools for security validation:
- Metasploit Framework: Comprehensive exploitation platform
- Burp Suite: Web application security testing
- Kali Linux: Security testing operating system with integrated tools
- Wireshark: Network protocol analyzer
- OWASP ZAP: Web application security scanner
Effective penetration testers typically employ 5-7 specialized tools during comprehensive assessments, with tool selection based on target environment characteristics.
AI-Enhanced Assessment Capabilities
Machine learning tools augmenting human analysis:
- Darktrace Enterprise Immune System: Autonomous detection of unusual network behavior
- IBM Watson for Cybersecurity: AI-assisted threat intelligence and analysis
- CylancePROTECT: AI-driven endpoint protection and assessment
- Vectra Cognito Platform: AI-based network detection and response
- Splunk Enterprise Security: Advanced analytics for security monitoring
Organizations integrating AI into their assessment processes report 63% faster analysis of complex environments and 47% improved detection of sophisticated attack patterns.
Evaluating Key Security Domains
Network Security Assessment
Evaluating network infrastructure protection:
- Perimeter Security: Firewalls, gateways, and boundary protection
- Network Segmentation: Internal separation and access controls
- Traffic Analysis: Monitoring and inspection capabilities
- Remote Access: VPN and remote connection security
- Wireless Networks: WiFi and cellular connectivity protection
Network security assessments should include evaluation of both north-south (external-internal) and east-west (internal) traffic controls, with particular focus on segmentation effectiveness.
Cloud Security Assessment
Addressing unique cloud environment risks:
- Identity and Access Management: User privileges and authentication controls
- Data Protection: Encryption and access controls for cloud-stored information
- Configuration Management: Security settings and hardening
- Container Security: Protection for containerized applications
- Serverless Function Security: Evaluation of function-as-a-service implementations
According to recent research, misconfigurations remain the leading cause of cloud security incidents, with 67% of breaches involving improperly configured cloud resources.
Application Security Assessment
Examining software security throughout the development lifecycle:
- Static Application Security Testing (SAST): Code analysis for vulnerabilities
- Dynamic Application Security Testing (DAST): Runtime application testing
- Software Composition Analysis: Evaluation of third-party components
- API Security Testing: Assessment of application programming interfaces
- Mobile Application Security: Evaluation of mobile app security controls
Organizations integrating security assessments throughout the software development lifecycle identify vulnerabilities at 1/30th the cost of fixing issues in production.
Operational Technology and IoT Assessment
Evaluating specialized systems and connected devices:
- Industrial Control Systems: Security of operational technology
- Internet of Things Devices: Connected device protection
- Medical Devices: Healthcare technology security
- Building Management Systems: Facility automation security
- SCADA Systems: Industrial monitoring and control
OT/IoT assessments require specialized methodologies, with 82% of organizations reporting that traditional IT assessment approaches are insufficient for these environments.
Analyzing and Reporting Assessment Results
Effective Result Interpretation
Transform raw findings into actionable intelligence:
- Pattern Recognition: Identify common vulnerability themes
- Root Cause Analysis: Determine underlying security issues
- Control Gap Identification: Pinpoint missing or ineffective controls
- Historical Comparison: Analyze trends from previous assessments
- Peer Benchmarking: Compare results to industry standards
Organizations performing comprehensive analysis beyond simple vulnerability listing achieve 74% more effective remediation and 53% better long-term security improvements.
Creating Impactful Security Assessment Reports
Structure reports for maximum effectiveness:
- Tiered Content: Provide executive, management, and technical views
- Business Context: Connect findings to business risks and impacts
- Visual Representations: Use charts and graphics to illustrate key points
- Clear Remediation Paths: Provide specific, actionable recommendations
- Prioritized Findings: Organize issues by risk level and remediation complexity
Effective security assessment reports include specific remediation recommendations for at least 95% of identified vulnerabilities, with clear ownership assignments and suggested timelines.
Developing Remediation Strategies
Transform findings into improvement plans:
- Immediate Actions: Quick fixes for critical vulnerabilities
- Short-Term Improvements: Tactical solutions for significant issues
- Long-Term Projects: Strategic improvements to security architecture
- Compensating Controls: Alternative protections when direct remediation isn’t feasible
- Exception Management: Process for accepting and documenting residual risks
Organizations with structured remediation approaches complete 73% more security improvements within 90 days compared to those without formal remediation planning.
Implementing Continuous Assessment Practices
Moving Beyond Point-in-Time Assessments
Evolve to ongoing security validation:
- Continuous Vulnerability Scanning: Regular automated discovery of weaknesses
- Security Validation Platforms: Tools that consistently test control effectiveness
- Breach and Attack Simulation: Automated and continuous security testing
- Continuous Control Monitoring: Real-time visibility into security control status
- DevSecOps Integration: Security assessment within development pipelines
According to recent data, organizations implementing continuous assessment practices identify critical vulnerabilities 27 days faster on average than those using traditional periodic assessments.
Integration with Security Operations
Connect assessment activities with ongoing security:
- Security Information and Event Management (SIEM) Integration: Correlate assessment data with security events
- Security Orchestration, Automation and Response (SOAR): Automate assessment-driven response actions
- Threat Intelligence Correlation: Link assessment findings with current threat data
- Vulnerability Management Workflows: Streamline from discovery to remediation
- Knowledge Management: Maintain assessment findings in centralized security knowledge base
Organizations with integrated assessment and operations report 68% faster remediation of critical vulnerabilities and 57% lower likelihood of repeated security issues.
Measuring Assessment Effectiveness
Evaluate the impact of your security assessment program:
- Coverage Metrics: Percentage of environment being assessed
- Time to Identify: Speed of vulnerability discovery
- Time to Remediate: Efficiency of fixing discovered issues
- Risk Reduction: Measurable improvements in security posture
- Assessment ROI: Business value delivered through assessment activities
Leading organizations measure and report on 7-10 key assessment performance indicators, with quarterly executive reviews of program effectiveness and value delivery.
Overcoming Common IT Security Assessment Challenges
Managing Assessment Scope in Complex Environments
Navigate complicated IT landscapes effectively:
- Risk-Based Scoping: Focus on highest-risk systems first
- Incremental Assessment: Divide large environments into manageable segments
- Automated Discovery: Use tools to map complex environments
- Federated Assessment: Distribute evaluation responsibilities across teams
- Continuous Expansion: Gradually increase coverage over multiple assessment cycles
Organizations using risk-based scoping approaches report 64% higher satisfaction with assessment outcomes while using 47% fewer resources compared to attempting complete coverage immediately.
Balancing Security Assessment with Business Operations
Minimize operational impact during assessments:
- Off-Hours Testing: Conduct intrusive tests during maintenance windows
- Production Safeguards: Implement controls to prevent business disruption
- Coordinated Scheduling: Align with business activity calendars
- Graduated Testing: Begin with low-impact methods before more intrusive evaluation
- Parallel Environments: Test replica systems when possible
According to industry surveys, 73% of organizations now conduct over half of their assessment activities with zero impact on business operations, compared to just 28% in 2020.
Addressing Resource and Expertise Constraints
Overcome common limitations:
- Automation Leverage: Maximize use of automated assessment tools
- Managed Services: Utilize external expertise for specialized assessments
- Prioritized Approach: Focus resources on highest-value assessment activities
- Tool Consolidation: Reduce complexity through integrated platforms
- Knowledge Transfer: Build internal capabilities through structured learning
Organizations implementing these strategies report achieving comprehensive security assessment coverage with 43% fewer specialized security resources compared to traditional approaches.
Conclusion: Building a Mature IT Security Assessment Program
Implementing effective IT security assessments is not a one-time project but an ongoing program that evolves with your organization and the threat landscape. By following the structured approach outlined in this guide—from careful preparation and methodology selection through execution, analysis, and continuous improvement—you can develop assessment capabilities that provide genuine security value and risk reduction. Remember that the most effective assessment programs balance technical thoroughness with business context, ensuring that security investments align with organizational priorities.
As you work to enhance your organization’s security assessment practices, focus on building repeatable processes, leveraging appropriate tools, and gradually increasing maturity through continuous refinement. Track your progress not just through vulnerability metrics but through meaningful risk reduction and business protection outcomes. With diligent application of these principles, your security assessment program can become a strategic advantage rather than merely a compliance exercise.
Ready to transform your IT security assessment approach? YuzTech’s cybersecurity experts can help you design, implement, and optimize assessment programs tailored to your specific environment and security objectives. Contact us today for a complimentary consultation and discover how our proven methodologies can enhance your security posture through effective, business-aligned IT security assessments.

