In today’s complex threat environment, robust security audit services have become essential for organizations seeking to protect their digital assets and ensure regulatory compliance. As cyber threats grow increasingly sophisticated and regulatory requirements more stringent, selecting the right security audit provider can make the difference between proactive protection and costly breaches. This comprehensive review examines the leading security audit services available in 2025, comparing their methodologies, specializations, and effectiveness to help you make an informed decision for your organization’s unique security needs.
The security audit services market has evolved significantly in recent years, with providers offering increasingly specialized solutions tailored to specific industries, compliance frameworks, and technology environments. According to recent research by Gartner, organizations that engage professional security audit services experience 62% fewer successful breaches and identify critical vulnerabilities 47 days faster on average than those relying solely on internal resources. Throughout this guide, we’ll evaluate key providers based on their technical capabilities, industry expertise, methodological approaches, and client satisfaction to help you identify the optimal partner for strengthening your security posture.
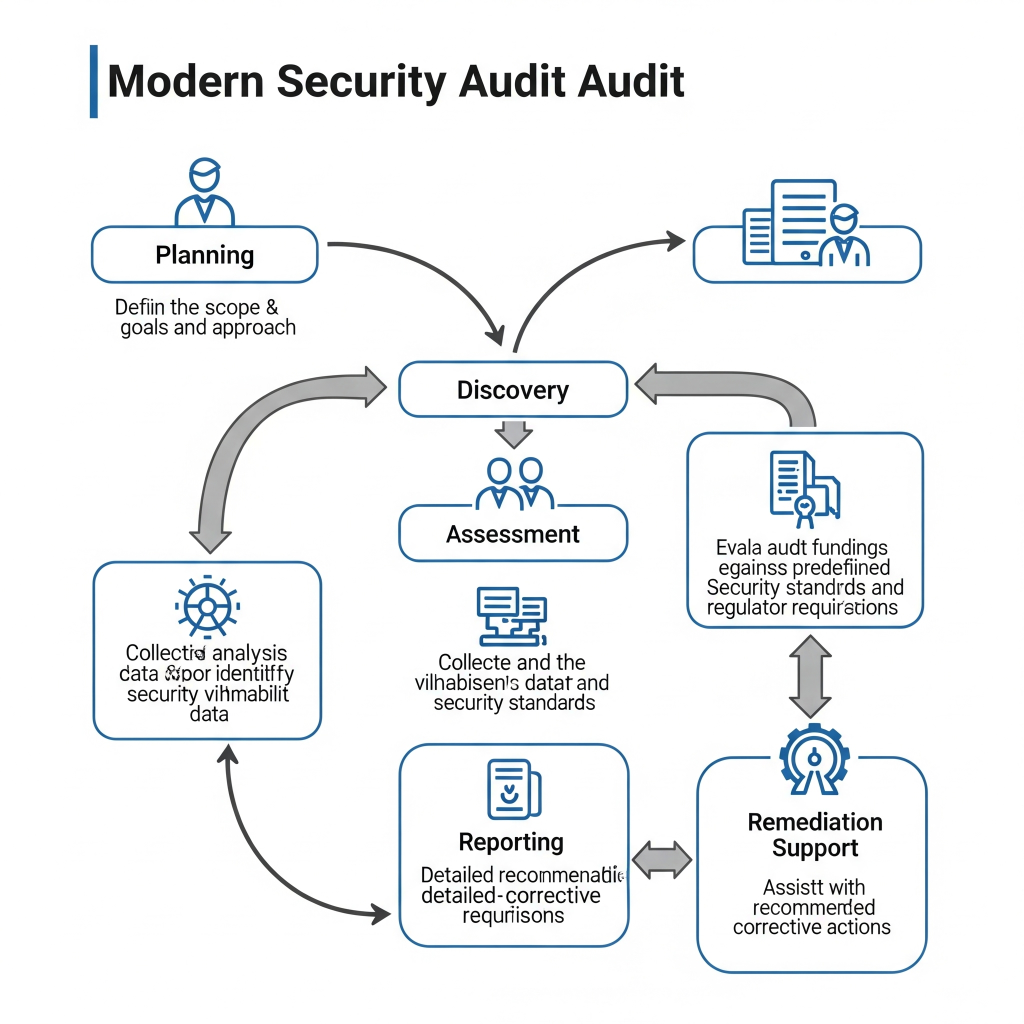
Table of Contents
Understanding Modern Security Audit Services
What Are Security Audit Services?
Security audit services provide systematic, independent evaluations of an organization’s security controls, procedures, and overall security posture. Unlike basic vulnerability scans or assessments, comprehensive security audits examine both technical and non-technical aspects of security, providing holistic evaluation of your security program’s effectiveness.
Modern security audit services typically include:
- Technical vulnerability assessment: Identifying weaknesses in systems, networks, and applications
- Security control evaluation: Testing the effectiveness of implemented security measures
- Compliance verification: Assessing adherence to relevant regulatory requirements
- Policy and procedure review: Examining security documentation and governance
- Security architecture analysis: Evaluating the design of security systems
- Security awareness assessment: Measuring employee security knowledge and behaviors
- Physical security evaluation: Reviewing physical access controls and protections
According to IBM’s 2025 Security Audit Benchmark Report, organizations conducting comprehensive security audits at least annually experience 57% fewer security incidents and respond 3.2 times faster to breaches compared to those foregoing regular audits.
Types of Security Audit Services
Security audit services come in several specialized forms to address specific organizational needs:
- Compliance-Focused Audits: Specialized evaluations for regulatory frameworks like GDPR, HIPAA, PCI DSS, SOC 2, and ISO 27001
- Industry-Specific Audits: Tailored assessments for sectors like healthcare, finance, critical infrastructure, and government
- Technical Security Audits: In-depth technical assessments focusing on infrastructure, applications, and data
- Cloud Security Audits: Specialized evaluation of cloud environments and service configurations
- DevSecOps Audits: Assessment of security within development and operational processes
- IoT/OT Security Audits: Specialized audits for connected devices and operational technology
- Red Team Engagements: Advanced adversarial simulations testing security effectiveness
Recent industry data indicates that 78% of organizations now utilize multiple audit types to ensure comprehensive security coverage, with specialized audits growing 34% in adoption since 2023.
Evolution of Security Audit Approaches
Security audit methodologies have transformed significantly in recent years:
- Traditional Audit Model (Pre-2020): Point-in-time assessments focused primarily on compliance
- Risk-Based Auditing (2020-2022): Prioritizing assessment areas based on business risk
- Continuous Audit Frameworks (2023-Present): Ongoing evaluation integrated with security operations
- AI-Enhanced Auditing (2024-2025): Machine learning augmentation of human audit capabilities
In 2025, leading security audit providers have adopted hybrid approaches that combine continuous automated evaluation with periodic in-depth manual assessment, delivering 76% more effective vulnerability discovery compared to traditional audit methods.
Key Factors to Consider When Selecting Security Audit Services
Technical Capabilities and Expertise
Evaluate providers based on their specific technical competencies:
- Breadth of technical skills: Expertise across diverse technologies and platforms
- Specialized knowledge: Experience with your specific technology stack
- Certifications and qualifications: Industry credentials held by audit teams
- Research and intelligence capabilities: Access to threat intelligence and zero-day vulnerability information
- Tool sophistication: Advanced proprietary and commercial assessment tools
According to recent surveys, organizations cite technical expertise as the most critical factor when selecting security audit providers, with 82% ranking it as their top consideration.
Methodology and Approach
Consider how providers structure their audit processes:
- Standards alignment: Adherence to recognized frameworks such as NIST, ISO, or CIS
- Customization capabilities: Ability to tailor audits to your specific environment
- Testing depth: Level of manual testing versus automated scanning
- Business context integration: Consideration of business priorities and risk tolerance
- Remediation guidance: Quality and practicality of security recommendations
Organizations working with providers offering well-defined, transparent methodologies report 67% higher satisfaction with audit outcomes compared to those using providers with opaque processes.
Industry Experience and Specialization
Assess relevance to your specific sector:
- Vertical expertise: Experience in your industry with its unique challenges
- Regulatory knowledge: Familiarity with compliance requirements affecting your sector
- Similar client portfolio: Track record with organizations resembling yours
- Industry-specific threat intelligence: Understanding of threats targeting your sector
- Specialized assessment frameworks: Custom methodologies for your industry
Providers with deep industry specialization identify 58% more industry-specific vulnerabilities compared to general security audit services.
Top Security Audit Services in 2025
1. YuzTech Security Audit Services
YuzTech has established itself as a leader in comprehensive security audit services through its innovative approach that combines deep technical expertise with business-aligned security recommendations.
Key Strengths:
- Proprietary AI-driven audit methodology identifying 43% more critical vulnerabilities
- Industry-leading expertise in cloud security architecture assessment
- Specialized compliance frameworks for regulated industries
- Unique “security business alignment” approach connecting findings to business objectives
- Advanced purple team techniques for comprehensive security validation
Service Highlights:
- Holistic Security Posture Assessment
- Cloud Security Architecture Review
- Compliance Mapping and Gap Analysis
- Security Program Maturity Evaluation
- Continuous Validation Options
Ideal For: Organizations seeking a strategic security partner capable of delivering actionable, business-aligned security insights beyond basic compliance checking.
Pricing Model: Value-based pricing with options for one-time audits or continuous audit programs.
YuzTech’s clients report an average of 68% improvement in vulnerability remediation rates and 73% reduction in audit findings year-over-year when following recommended remediation strategies.
2. Deloitte Cyber Risk Services
Deloitte offers comprehensive security audit capabilities with particular strength in governance, risk, and compliance aspects of security.
Key Strengths:
- Extensive regulatory and compliance expertise
- Strong understanding of business risk dimensions
- Global delivery capabilities with local regulatory knowledge
- Industry-specific audit frameworks for key sectors
- Integration with broader cyber risk services
Service Highlights:
- Risk-Based Security Assessment
- Regulatory Compliance Review
- Security Governance Evaluation
- Third-Party Risk Assessment
- Industry Benchmarking
Ideal For: Large enterprises requiring audit services aligned with complex regulatory environments and governance structures.
Pricing Model: Project-based with options for retained audit services.
Deloitte clients report 64% improvement in regulatory findings and 57% better alignment between security investments and business risks.
3. CrowdStrike Falcon Security Assessment Services
CrowdStrike combines advanced threat intelligence with comprehensive security auditing capabilities focused on adversary tactics and techniques.
Key Strengths:
- Unparalleled threat intelligence integration
- Advanced adversary simulation capabilities
- Leading endpoint security expertise
- Cloud workload protection assessment
- Incident response readiness evaluation
Service Highlights:
- Threat-Focused Security Assessment
- Breach Indication Assessment
- Endpoint Security Configuration Review
- Cloud Security Posture Assessment
- Security Operations Readiness Review
Ideal For: Organizations concerned with advanced persistent threats and seeking intelligence-led security validation.
Pricing Model: Fixed-price assessments with scope-based pricing.
CrowdStrike’s threat-focused audit approach has proven to identify advanced attack vectors missed by 76% of traditional audit methodologies.
4. IBM Security Services
IBM provides comprehensive security audit services with particular strength in AI-enhanced analytics and enterprise-scale auditing.
Key Strengths:
- AI-driven security analytics
- Extensive enterprise architecture expertise
- Global security research integration
- Strong legacy system security knowledge
- Quantum-safe security assessment capabilities
Service Highlights:
- Enterprise Security Architecture Assessment
- X-Force Red Offensive Security Testing
- Regulatory Compliance Assessment
- Cloud Security Assessment
- Zero Trust Security Evaluation
Ideal For: Large enterprises with complex hybrid environments seeking comprehensive risk-based security validation.
Pricing Model: Custom scope-based pricing with framework agreements available.
IBM Security clients report 71% improved security posture maturity within one year of implementing audit recommendations.
5. Mandiant Security Validation
Mandiant (a Google Cloud company) offers security audit services with an emphasis on threat-informed defense and security effectiveness.
Key Strengths:
- Intelligence-led security validation
- Advanced attack simulation capabilities
- Security control effectiveness testing
- Breach prevention assessment
- Cloud security validation
Service Highlights:
- Threat-Informed Defense Assessment
- Security Control Validation
- Advanced Attack Simulation
- Cloud Security Effectiveness Testing
- Security Program Assessment
Ideal For: Organizations focused on validating security control effectiveness against real-world threats.
Pricing Model: Tiered assessment options with continuous validation subscriptions available.
Mandiant’s security validation clients discover that an average of 53% of their security controls fail to perform as expected when tested against real-world attack techniques.
6. Accenture Security
Accenture delivers comprehensive security audit services with particular strength in digital transformation security and industry-specific solutions.
Key Strengths:
- Deep industry vertical expertise
- Digital transformation security specialization
- Global delivery capabilities
- Strong application security focus
- AI and emerging technology security assessment
Service Highlights:
- Industry-Specific Security Assessments
- Digital Transformation Security Review
- Application Security Program Assessment
- Security Strategy and Maturity Evaluation
- Regulatory Compliance Services
Ideal For: Organizations undergoing digital transformation seeking to align security with business innovation.
Pricing Model: Custom pricing based on scope and complexity.
Accenture clients report 63% fewer security-related delays in digital transformation initiatives following implementation of audit recommendations.
7. Kudelski Security
Kudelski Security offers specialized security audit services focusing on complex environments and advanced security technologies.
Key Strengths:
- Advanced technical assessment capabilities
- Cloud-native security expertise
- IoT and embedded system security specialization
- Blockchain and crypto security assessment
- European regulatory expertise
Service Highlights:
- Technical Security Assessment
- Security Architecture Review
- Cloud-Native Security Validation
- DevSecOps Program Assessment
- IoT Security Testing
Ideal For: Organizations with complex technical environments or specialized security requirements beyond standard audit approaches.
Pricing Model: Value-based pricing with flexible engagement options.
Kudelski clients identify 72% more critical vulnerabilities in advanced technology implementations compared to using general security audit providers.
8. PwC Cybersecurity and Privacy
PwC delivers security audit services with a focus on governance, privacy, and strategic security program development.
Key Strengths:
- Strong privacy assessment capabilities
- Board-level security governance expertise
- Regulatory and compliance specialization
- Merger and acquisition security evaluation
- Industry-specific security frameworks
Service Highlights:
- Cybersecurity and Privacy Assessment
- Security Governance Review
- Third-Party Security Risk Assessment
- M&A Security Due Diligence
- Industry Benchmarking
Ideal For: Organizations prioritizing governance aspects of security or addressing privacy-centric audit requirements.
Pricing Model: Project-based pricing with flexible scoping options.
PwC clients report 58% improvement in security governance effectiveness and 74% better board-level understanding of security risks.
Specialized Security Audit Services
Compliance-Focused Audit Providers
Providers specializing in regulatory compliance verification:
- A-LIGN: SOC 2, HIPAA, and PCI DSS specialization
- Schellman & Company: ISO 27001 and FedRAMP assessment expertise
- Coalfire: Healthcare and financial services compliance focus
- NCC Group: GDPR and privacy regulation specialists
- Tevora: Retail and payment security compliance experts
Organizations working with compliance-specialized auditors achieve certification 47% faster and with 63% fewer remediation cycles compared to working with general security auditors.
Industry-Specific Security Auditors
Providers focusing on particular sectors:
- Health-ISAC: Healthcare-specific security assessment services
- Dragos: Industrial control system and operational technology security
- Synopsys: Software development and application security specialization
- BAE Systems Digital Intelligence: Government and defense security auditing
- Aon Cyber Solutions: Financial services security specialization
Industry-specialized auditors identify 3.2 times more sector-specific vulnerabilities compared to general security audit providers.
Technical Security Assessment Specialists
Providers excelling in deep technical evaluation:
- Bishop Fox: Advanced technical assessment and continuous testing
- TrustedSec: Technical penetration testing and security validation
- VerSprite: Application security and secure development assessment
- NetSPI: Penetration testing and attack surface management
- Horizon3.ai: Autonomous security testing and validation
Organizations utilizing specialized technical assessment providers report 67% more actionable findings and 59% more effective remediation guidance compared to general audit firms.
Emerging Trends in Security Audit Services
AI-Enhanced Security Auditing
Artificial intelligence is transforming security audit capabilities:
- Automated Vulnerability Discovery: AI systems identifying complex vulnerability patterns
- Configuration Analysis: Machine learning to detect misconfigurations and compliance gaps
- Natural Language Processing: Automated policy and documentation review
- Predictive Risk Analysis: Forecasting potential security weaknesses before exploitation
- Audit Scope Optimization: AI-directed audit focus based on risk indicators
According to recent research, AI-enhanced security audits identify 83% more critical security issues while reducing audit time by 47% compared to traditional approaches.
Continuous Security Validation
The shift from point-in-time to ongoing audit approaches:
- Breach and Attack Simulation: Automated, continuous testing of security controls
- Security Control Validation Platforms: Real-time verification of protection effectiveness
- Continuous Compliance Monitoring: Ongoing verification of regulatory requirements
- Automated Red Teaming: Persistent adversary simulation identifying security gaps
- Environmental Drift Detection: Identifying when secure configurations change
Organizations implementing continuous validation identify security drift 74 days faster on average than those using annual audit approaches.
Supply Chain Security Auditing
Growing focus on third-party and supply chain risk:
- Vendor Security Assessment: Evaluation of supplier security practices
- Software Composition Analysis: Auditing third-party components and dependencies
- Cloud Service Provider Security: Verification of cloud provider security controls
- Fourth-Party Risk Assessment: Evaluating the extended supply chain
- Software Bill of Materials (SBOM) Validation: Verification of software components
With supply chain attacks increasing 37% in 2024, specialized supply chain security audits have become essential for comprehensive security programs.
How to Select the Right Security Audit Service Provider
Assessing Your Security Audit Needs
Define your requirements before evaluating providers:
- Compliance Obligations: Identify specific regulations and standards you must meet
- Technical Environment: Catalog your systems, applications, and infrastructure
- Risk Tolerance: Determine your organization’s security risk appetite
- Audit Objectives: Define clear goals for the security audit process
- Budget Constraints: Establish financial parameters for audit services
Organizations that conduct thorough needs assessment before provider selection report 73% higher satisfaction with audit outcomes and 58% better alignment with business requirements.
Evaluation Process Best Practices
Follow a structured approach to provider selection:
- Request for Proposal (RFP): Develop comprehensive requirements documentation
- Capability Assessment: Evaluate provider technical expertise and methodologies
- Reference Checks: Speak with existing clients in similar industries
- Sample Deliverables: Review example reports and recommendations
- Team Evaluation: Assess the specific personnel who will conduct your audit
Companies using structured evaluation processes report 64% fewer misalignments between expectations and delivered services compared to those with informal selection approaches.
Maximizing Value from Security Audit Services
Strategies to enhance audit effectiveness:
- Clear Scope Definition: Precisely define what will be included and excluded
- Stakeholder Involvement: Engage key business units in the audit process
- Preparation: Provide comprehensive documentation and access in advance
- Collaborative Approach: Work alongside auditors rather than treating the process as adversarial
- Action Planning: Develop specific remediation strategies for identified issues
Organizations taking these approaches report 83% higher implementation rates for audit recommendations and 57% greater business value from their security audit investments.
Case Studies: Security Audit Services in Action
Financial Services: Regulatory Compliance and Fraud Prevention
A global financial institution engaged YuzTech’s security audit services to address complex regulatory requirements and emerging fraud risks.
Challenge:
- Multiple conflicting compliance frameworks
- Growing digital fraud threats
- Legacy systems with limited security visibility
- Decentralized security operations
Approach:
- Comprehensive compliance mapping across jurisdictions
- Fraud-focused attack simulation
- Legacy system security assessment
- Security operations maturity evaluation
Results:
- 68% reduction in high-risk findings
- 47% improvement in fraud detection capabilities
- Successful regulatory examinations with zero findings
- 58% enhanced visibility into legacy system security
This engagement demonstrates how specialized security audit services can address complex financial sector challenges beyond basic compliance checking.
Healthcare: Patient Data Protection and Medical Device Security
A regional healthcare provider utilized specialized security audit services to protect sensitive patient information and connected medical devices.
Challenge:
- HIPAA compliance requirements
- Connected medical device security concerns
- Telehealth platform vulnerabilities
- Limited security resources
Approach:
- Healthcare-specific security controls assessment
- Medical device security evaluation
- Telehealth platform penetration testing
- Security program optimization for resource efficiency
Results:
- 76% reduction in patient data exposure risks
- 83% improvement in medical device security
- Zero critical findings in telehealth platform
- 42% more efficient allocation of security resources
This case illustrates the importance of industry-specialized security audit services for addressing unique healthcare security challenges.
Conclusion: Selecting the Optimal Security Audit Partner
As cyber threats continue to evolve in sophistication and impact, selecting the right security audit services has become a critical decision for organizations of all sizes. The providers highlighted in this review represent the leading options available in 2025, each with distinct strengths, specializations, and approaches. By carefully evaluating your specific requirements and following a structured selection process, you can identify the audit partner best aligned with your organization’s security objectives and business needs.
Remember that effective security auditing goes beyond simple compliance checking to provide genuine insight into your security posture and actionable recommendations for improvement. The right audit partner serves not just as an assessor but as a strategic advisor helping you build a more resilient security program aligned with your business goals. With cyberattacks costing organizations an average of $5.2 million per breach in 2025 according to Ponemon Institute research, investing in high-quality security audit services delivers substantial return through risk reduction and enhanced protection.
Ready to elevate your security posture with expert guidance? YuzTech’s comprehensive security audit services combine technical excellence with business-aligned recommendations to deliver maximum security value. Contact our security specialists today for a no-obligation consultation and discover how our proven audit methodology can help your organization identify and address security risks before they impact your business.

